Watch out for the do-it-yourself Wordpress Designer, It is tough to be a security expert and Designer
 Monday, April 14, 2014 at 9:38AM
Monday, April 14, 2014 at 9:38AM Wordpress comes up regularly when people think about hosting a website or blog. It’s popular what is the problem? Netcraft has some data that will show you the problem. Security.
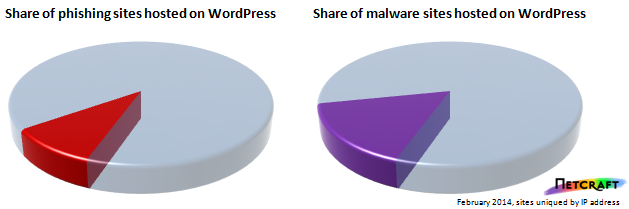
WordPress is the most common blogging platform and content management system in the world: Netcraft's latest survey found nearly 27 million websites running WordPress, spread across 1.4 million different IP addresses and 12 million distinct domain names. Many of these blogs are vulnerable to brute-force password guessing attacks by virtue of the predictable location of the administrative interface and the still widespread use of the default "admin" username.
But remarkably, not a single phishing site was hosted on Automattic's own WordPress.com service in February. WordPress.com hosts millions of blogs powered by the open source WordPress software. Customers can purchase custom domain names to use for their blogs, or choose to register free blogs with hostnames likeusername.wordpress.com.
If you are going to use wordpress try hard to use wordpress.com.
Vulnerable WordPress blogs can also be used for other nefarious purposes. A botnet of more than 162,000 WordPress blogs (less than 1% of all WordPress blogs) was recently involved in a distributed denial of service (DDoS) attack against a single website. Attackers exploited the Pingback feature in these WordPress blogs (which is enabled by default) to flood the target site with junk HTTP requests, causing it to be shut down by its hosting company.